EchoTrail Insights
The comprehensive Windows process behavior database that helps security teams understand what's normal to identify what's not.
Unlike threat intelligence that tells you what's bad, Insights tells you what's known-good—making threat detection faster and more accurate.
One Platform, Multiple Ways to Access
Choose How You Want to Use Insights
Whether you need manual search capabilities or automated API access, Insights adapts to your workflow.
- Web Search
Interactive search interface for manual investigations
- Search by filename or hash
- Detailed process descriptions
- Behavioral analytics and trends
- Security intelligence insights
- Parent-child process relationships
Free tier available
Start Searching- Scoring API
Real-time process scoring for automated workflows
- Submit process profiles for scoring
- Receive 0-100 commonality scores
- Custom environment baselines
- Bulk scoring capabilities
- SIEM/SOAR integration ready
API tiers available
View API Docs- Search API
Programmatic access to the full Insights database
- Query the complete database
- Automated enrichment workflows
- Advanced search capabilities
- Structured data responses
- High-volume access tiers
API tiers available
Explore API
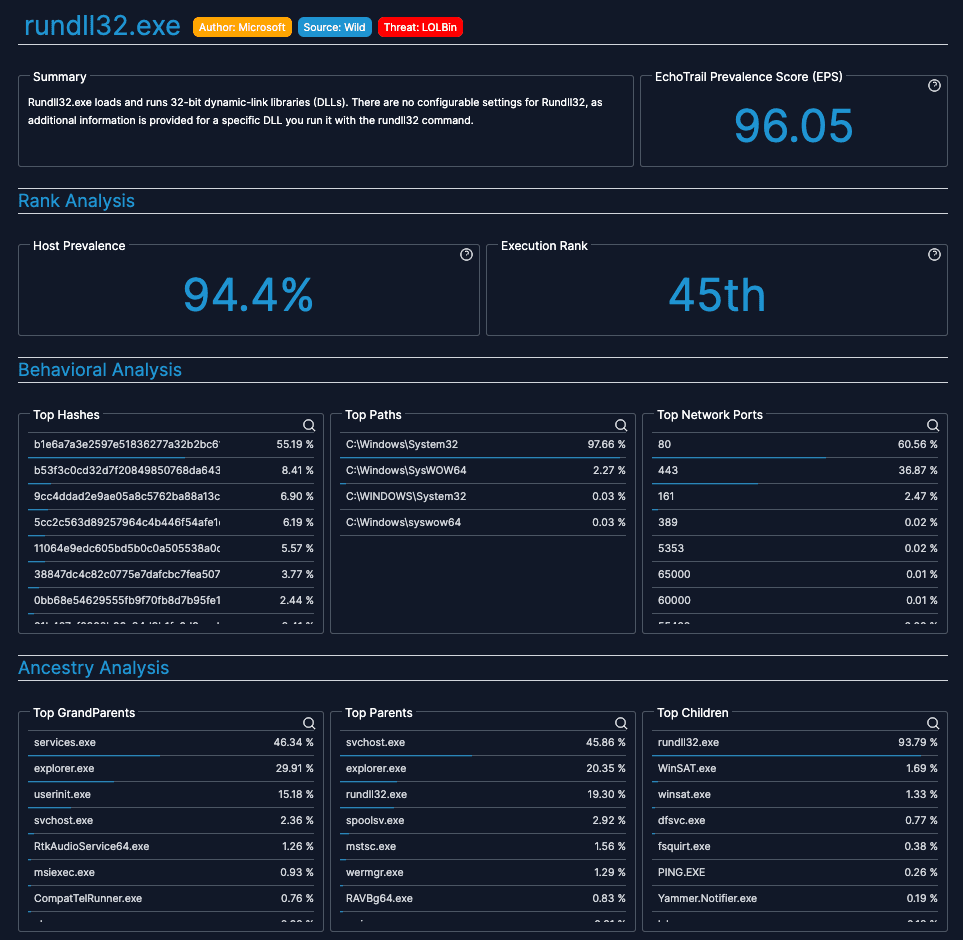
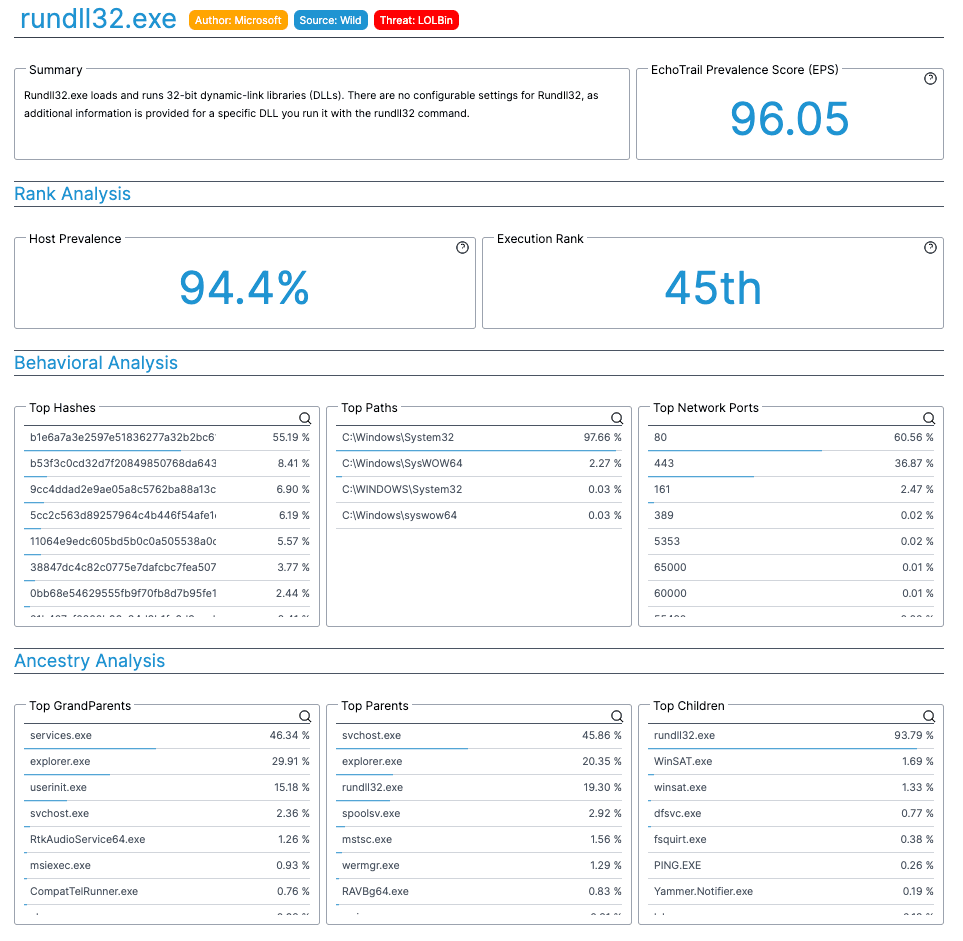
Interactive Search Experience
Understand Process Behavior Instantly
Search our comprehensive database to understand how Windows processes typically behave. Get descriptions, prevalence data, security intel, and behavioral patterns.
Analysts use Insights to answer:
- •What is this process and who wrote it?
- •How common is this across environments?
- •What are the typical execution patterns?
- •How can threat actors abuse this process?
Enter information about a process execution and get an anomaly score on the likelihood of it occurring, where 0 is very rare and 100 is exceedingly common.
Statistical Process Scoring
Know What's Normal in Your Environment
Submit process execution details and receive a score from 0-100 indicating how common that behavior is. Higher scores mean more common, lower scores indicate rare or unusual activity worth investigating.
Perfect for:
- SIEM/SOAR automated enrichment
- Alert triage and prioritization
- Threat hunting workflows
- Custom environment baselines
How Security Teams Use Insights
From SOC analysts to threat hunters, Insights helps teams work faster and more confidently.
- Alert Triage & Enrichment
Quickly determine if a process is known-good to resolve alerts faster
Example:
An analyst sees an alert for "svchost.exe" and uses Insights to confirm it's running from the expected path with normal behavior patterns.
- Threat Hunting
Identify rare or unusual process behaviors that warrant investigation
Example:
A threat hunter searches for processes with low scores to find potential living-off-the-land techniques or novel malware.
- Incident Response
Understand process relationships and identify anomalous behaviors during investigations
Example:
During an incident, responders use Insights to map out normal vs. abnormal process execution chains to understand the attack timeline.
EchoTrail Insights by the Numbers
Trusted by security teams worldwide for process intelligence
2.5M
Insight Searches
317M
Executions Analyzed
10M
Processes Scored
Start with Free Access, Scale with API Tiers
Begin exploring with our free search interface, then upgrade to API access for automated workflows. Our API bundles search and scoring for the best experience.
API access includes both search and scoring capabilities for comprehensive process intelligence.